Schedule A Demo
Start you journey to build an open, unified, and human-augmented autonomous SOC
"Sportscar Performance XDR for a Family Sedan Budget!"
...This was the best POC experience I have ever been through, and we threw your team through shards of glass."
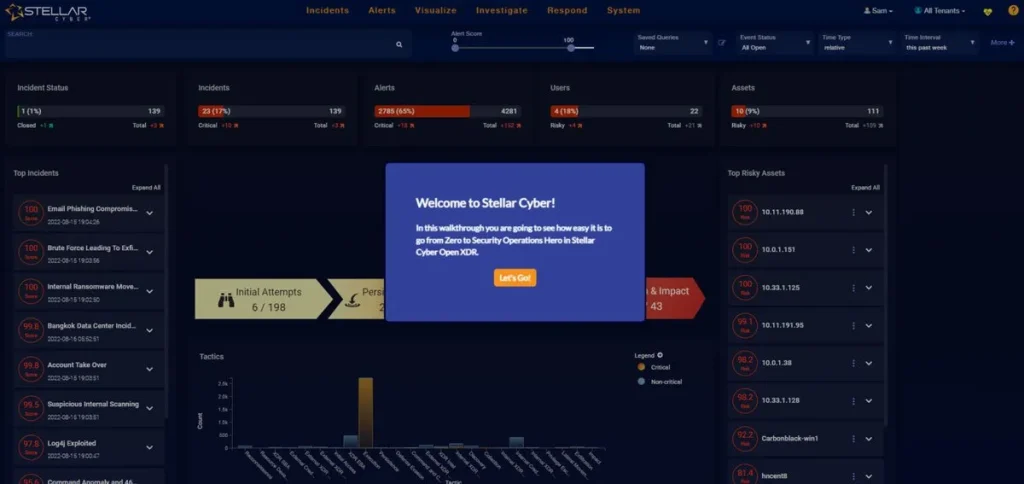
Explore the platform in 5 minutes.
See Why 14,000+ Customers Trust Stellar Cyber to Power SecOps.
Stellar Cyber’s patented Kill Chain Loop™ gives you real-time, end-to-end visibility into threat progression—leveraging the tools and data you already trust.
From initial access to lateral movement and impact, Stellar Cyber automatically correlates signals across your environment, cutting through the noise to highlight only high-fidelity, scored threats. Instead of managing thousands of alerts, security teams focus on a few actionable correlated Cases, driving faster, smarter, automation-driven response at scale.
Schedule A Demo
See how Stellar Cyber can provide real-time visibility, with AI-driven incident correlation and response to threats.
Please complete this form and a Stellar Cyber expert will contact you to schedule a demo.
Looking for Stellar Cyber Support?
Please sign in here, submit a ticket and one of our team members will contact you soon.
What Customers & Analysts Say.
"Sportscar Performance XDR for a Family Sedan Budget!"
Gartner Peer Insights
"The platform’s AI delivers a complete view of security events across our clients’ global infrastructure under one pane of glass"
Todd Willoughby
Director of Security & Privacy at RSM US
"Stellar Cyber delivers built-in Network Detection & Response (NDR), Next Gen SIEM and Automated Response"
Rik Turner
Senior Principal Analyst, Security and Technology

“Stellar Cyber is the most
cost-effective way to adopt
AI and XDR”
Erwin Eimers
CISO of Sumitomo Chemical
"Users can enhance their favorite EDR tools with full integration into an XDR platform, obtaining greater visibility."
Jon Oltsik
Senior Principal Analyst and ESG Fellow

"Stellar Cyber reduced our analysis expenses and enabled us to kill threats far more quickly."
Central IT Department
University of Zurich
Bring Hidden
Threats
to Light
Expose threats hiding in the gaps left by your current security products, making it harder for
attackers to harm your business.